Network Penetration Testing
 The process of identifying vulnerabilities, evaluating the risk, remediation, and reporting is called vulnerability management. By running penetration tests, organizations are able to more efficiently find and fix security vulnerabilities within their network.
The process of identifying vulnerabilities, evaluating the risk, remediation, and reporting is called vulnerability management. By running penetration tests, organizations are able to more efficiently find and fix security vulnerabilities within their network.




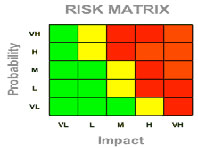 The process of understanding, assessing and managing risk is key to managing any business. In particular this process, as it relates to information, can help you to formulate your strategy for securing your business information assets.
The process of understanding, assessing and managing risk is key to managing any business. In particular this process, as it relates to information, can help you to formulate your strategy for securing your business information assets.